What Is an IP Address? Understanding How It Works, Different Types, and How to Protect It
An IP address, short for Internet Protocol address, is a unique identifier for a device connected to the internet or a network infrastructure. It is fundamental in facilitating communication and data transfer across devices online.
In this article, we’ll provide the IP address definition and explain how an IP address works. We’ll also explore how they contribute to the seamless flow of information across networks.
Additionally, this article will outline the different types of Internet Protocol addresses, discuss common IP address threats, and provide tips on securing an IP address to protect your online presence and confidential data.
Download Glossary For Web Beginners
What Is an IP Address?
An IP address is a string of numbers that works similarly to a home network or email address, ensuring the correct data is sent to the right computer. In other words, it functions as a communication medium for devices online.
How Do IP Addresses Work
The Internet Protocol works by transmitting data packets over connected networks.
When you visit a website using a computer or mobile phone, your device needs to find where the website’s data is located in order to retrieve it.
First, the computer connects to a network router, usually provided by an internet service provider (ISP). The router will then communicate with the server where the website is stored to access the files that need to be sent back to your computer.
The computer, router, and server each have specific IP addresses that can be recognized by one another. It is through those IP addresses that internet-connected devices can communicate as well as retrieve and send data.
IPv4 vs IPv6
IPv4 is short for Internet Protocol version 4 and is the most widely used. It is a 32-bit number system divided into four parts (octets) separated by dots. The value of each octet varies from 0 to 255. As such, there are approximately 4.3 billion unique IPv4 addresses.
Here’s an example of what an IPv4 looks like:
169.89.131.246
All types of systems handle IPv4 routing without problems. That’s because IPv4 supports most network topologies because of its simple prefixes. Also, data packets are well encrypted to ensure safe communication between networks.
However, the most recent version of the Internet Protocol is IPv6, intended to replace IPv4. This is because the number of IPv4 variations is running out, mainly due to how fast the internet is expanding.
The Internet Engineering Task Force designed IPv6 addresses to be 128-bit long.
This means there are around 340 undecillion unique IPv6 addresses, written in eight sets of 16-bit hexadecimal digits separated by colons. You will see letters from A to F in an IPv6 address.
Below is an example of an IPv6 address:
2001:3FFE:9D38:FE75:A95A:1C48:50DF:6AB8
IPv6 includes built-in Internet Protocol Security (IPSec) support, offering more robust security than IPv4. IPSec provides confidentiality, authentication, and data integrity, ensuring secure communication over IPv6 networks.
Let’s review some key benefits of IPv6:
- More efficient routing. IPv6 enables more efficient routing by reducing the size of routing tables and enabling hierarchical routing. ISPs can aggregate the prefixes of customer networks into a single prefix, simplifying routing and improving scalability.
- More efficient packet processing. Unlike its older counterpart, IPv6 does not have an IP checksum, resulting in more efficient data packet processing. It also does not support the broadcast address system. IPv6 uses multicast, which optimizes network bandwidth utilization.
- Simplified network configuration. IPv6 includes built-in address auto-configuration. It removes the need for manual configuration or the reliance on Dynamic Host Configuration Protocol (DHCP) servers. This feature allows devices to generate unique IPv6 addresses based on certain parameters and rules.
- Support for new services. This new IP version eliminates the need for Network Address Translation (NAT), restoring true end-to-end connectivity at the IP layer. This supports new service development and deployment requiring direct connections between devices, including peer-to-peer networks.
These benefits strengthen IPv6 as a protocol to address the limitations of IPv4 and support the internet’s future growth and connectivity needs.
Types of IP Addresses
In this section, we’ll look at six IP address types, from private to public and unique IP addresses.
Private IP Address
A private IP address is a reserved address used within a local network for communication among authorized devices. It’s assigned by a router or a network administrator, following specific ranges defined by the Internet Assigned Numbers Authority (IANA).
These addresses are not directly accessible on the internet. By keeping internal network devices hidden, private IP addresses offer an additional layer of security.
As a result, private IP addresses enable devices within a local network, typically in homes and offices, to communicate securely with each other.
Public IP Address
A public IP address refers to a globally unique address assigned to a networked device, enabling communication between one device to another across the internet.
Your device, for example, uses its public IP address to establish an internet connection when you access a website, send an email, or connect to a remote server. Consequently, these addresses can be used to identify and trace your online activity.
Public IP addresses are assigned by Internet Service Providers (ISPs) and are visible on the internet. Depending on the ISP’s allocation policy, they can be static or dynamic.
Dynamic IP Address
A dynamic IP address changes each time a device connects to the network.
These addresses are typically assigned by the ISP’s DHCP server. So, when your device connects to the internet, the DHCP server assigns a temporary IP address to it.
Typically, a home IP address and company network connection use dynamic addresses. They are cost-effective as ISPs can assign a limited number of IP addresses to a larger pool of users.
The dynamic nature of these addresses promotes stronger security. They make it harder for threat actors to breach the network interface. However, dynamic IP addresses make it more challenging for most internet users to host services or access a device remotely.
Static IP Address
A static IP address is a fixed or consistent IP address assigned to a device that remains constant over time. Unlike the periodically-changing dynamic IP address, a static IP address ensures consistency unless manually reconfigured.
Static IP addresses are widely used to host websites, email servers, and other services requiring a predictable address. They are advantageous for remote access and advanced network configurations.
To obtain a static address, request one from your internet service provider. However, static IP addresses may come at an additional cost and are less commonly used by regular users.
Shared IP Address
A shared IP address can be used by multiple devices or websites simultaneously.
Shared IP addresses are commonly used in web hosting environments, where multiple websites are hosted on the same web server. The server distinguishes those websites based on other information, such as the domain name.
These IP addresses are cost-effective, as many websites can share the same web servers and resources. However, they may have limitations in terms of advanced functionalities and customization options. This is because all websites that share the same IP address will be subject to the same restrictions.
Dedicated IP Address
A dedicated IP address is exclusively assigned to a single device or website.
Unlike shared IP addresses, this unique IP address cannot be used for any other device or website, offering a more secure and reliable connection.
That way, your site can be accessed by the IP address alone instead of its domain name. Furthermore, it’s possible to run your own File Transfer Protocol (FTP) server.
Dedicated IP addresses also offer more control and flexibility than the shared type. These addresses are often used for specific purposes, such as running applications requiring direct access or SSL certificate installation.
Dedicated IP addresses are typically available as an additional service from your hosting provider or ISP. At Hostinger, you can get a dedicated IP address for free by purchasing our Cloud hosting or VPS hosting plans.

IP Address Allocation
Regional Internet Registries (RIRs) help allocate and register internet number resources within specific regions. The organization ensures the efficient and fair distribution of these resources, including IP addresses.
There are five recognized RIRs worldwide, each serving a specific geographical region:
- African Network Information Centre (AFRINIC) for Africa.
- American Registry for Internet Numbers (ARIN) for the US, Canada, Antarctica, and parts of the Caribbean.
- Asia Pacific Network Information Centre (APNIC) for East Asia, Oceania, South Asia, and Southeast Asia.
- Latin America and Caribbean Network Information Centre (LACNIC) for Latin America and most of the Caribbean.
- Réseaux IP Européens Network Coordination Centre (RIPE NCC) for Europe, Central Asia, Russia, and West Asia.
Regarding IP addresses, here is the allocation:
- Private IP addresses are assigned to devices by a router via the DHCP. They can also be manually set once the connected devices can communicate within the local networks.
- Public IP addresses are allocated to a device by an ISP. Internet activity from the device is routed through the ISP and back to the device using the assigned public IP address.
- Dynamic IP addresses on a local network are typically assigned by a network router. In the case of networks connected to the internet, an ISP assigns dynamic IP addresses to its clients’ computers.
- Static IP addresses can be set through the operating system’s network settings or the router’s configuration page.
How to Check My IP Address
There are several ways to conduct an IP address lookup for your devices. However, to check a device’s private IP address, the steps may vary depending on the platform.
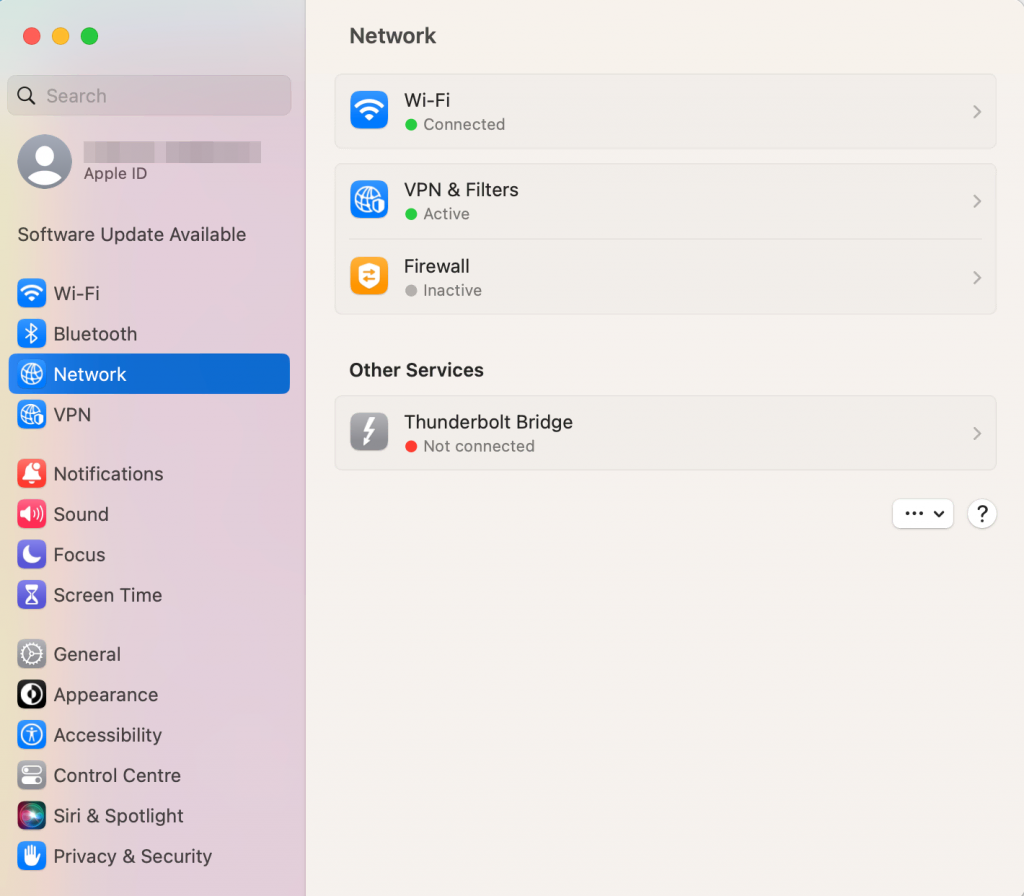
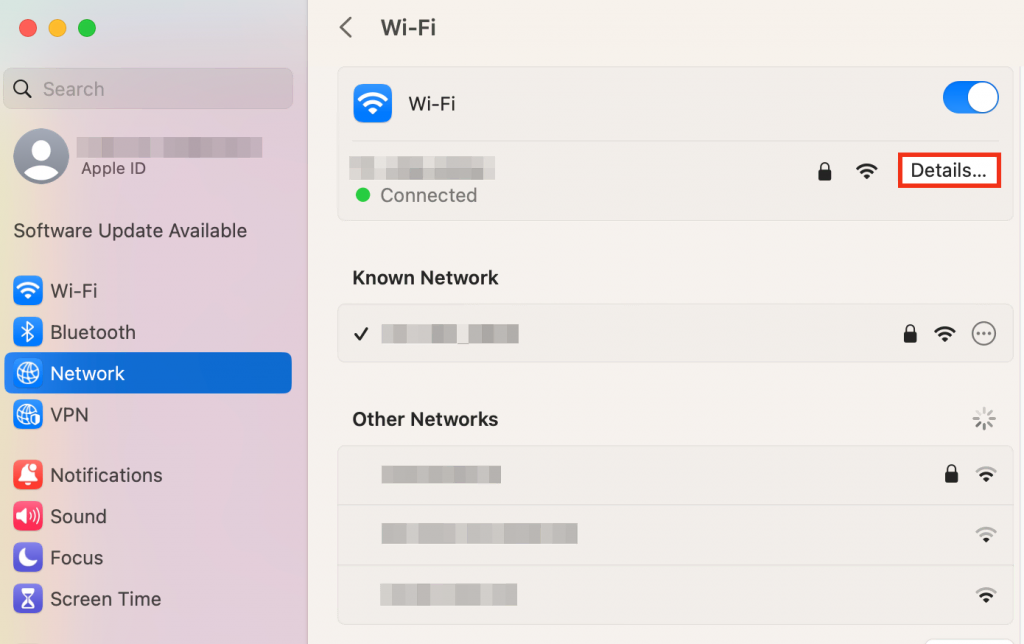
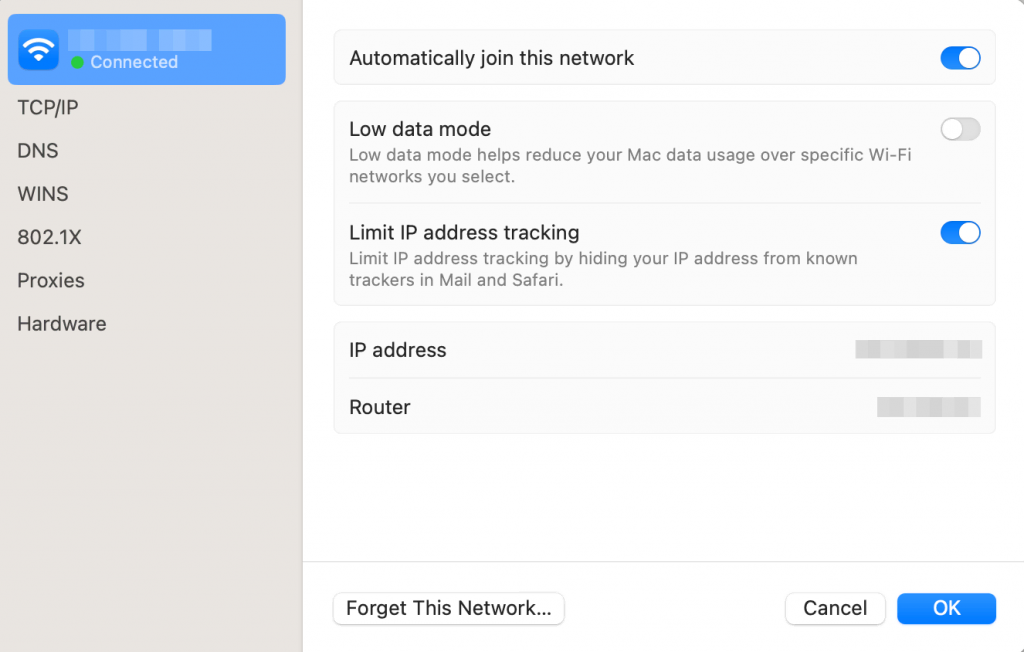
Here’s how to find your IP address on macOS:
- Access System Preferences and select Network.
- Choose the network, for example, Wi-Fi. Then, click Details.
- Locate your IP address above the Router section.
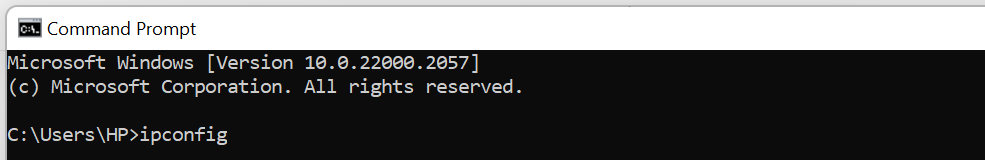
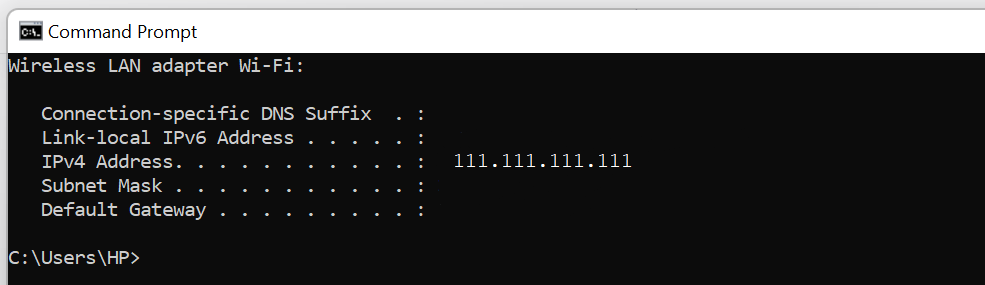
Here’s a simple guide for finding your IP address on Windows:
- Open Command Prompt by typing cmd in the Windows search bar.
- Type ipconfig and press Enter.
- Scroll down until you find your IP address listed in the IPv4 Address section.
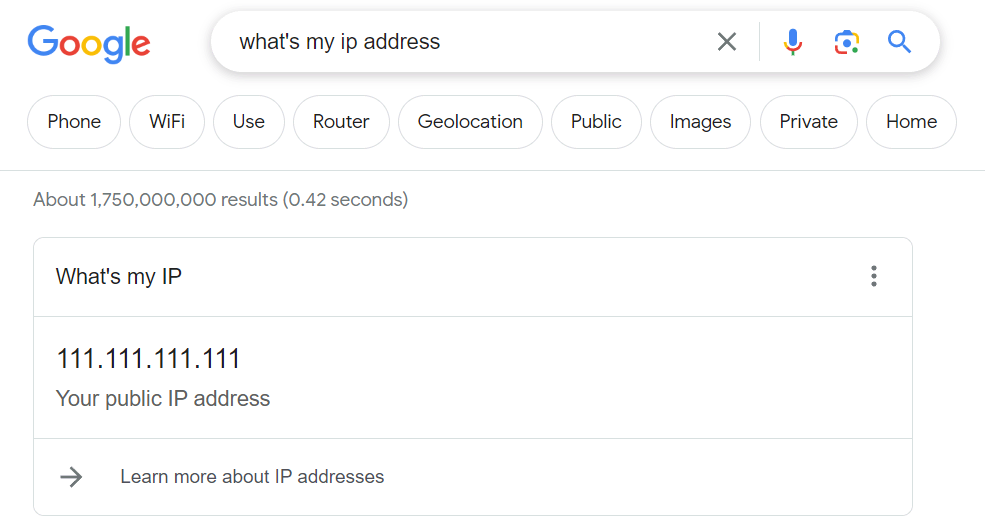
To check your public IP, search “what is my IP address” on Google. The search result page will immediately show your public IP address.
Common IP Address Security Threats
Protecting your IP address and not sharing it with anyone is crucial. If a threat actor discovers it, they can use the address for various cyber attacks. Though an IP address doesn’t contain sensitive information, it can still be used to:
- Find your actual address. IP addresses show geolocations, enabling a person with bad intentions to identify the city, region, and physical address of your company or home. This can lead to stalking, pranks, or even theft.
- Track your online activity. Hackers can monitor your internet activity if they obtain your IP address. They may track your online purchases, payments, or credit card information. These pieces of information enable hackers to steal your identity or sell them for profit.
- Hack your devices. Your computer or mobile connects to the internet through IP addresses and ports. Hackers who know your IP address can brute-force the connection through the ports, taking over your networked device. As a result, sensitive information like passwords and financial details can be at risk.
- Use your resources or frame you. Cyber criminals can use your IP address to conduct malicious activities, framing you in the process. For example, they might download or upload illegal content using your IP address, which can result in a denial of service or even legal issues.
How to Protect Your IP Address
Since an IP address and internet privacy are closely linked, there are several measures you can take to safeguard your online identity and maintain your privacy. Here are three tips for protecting your IP address.
Use a VPN
A VPN, short for Virtual Private Network, provides a safer online experience as it hides your actual IP address by redirecting the data and traffic through an encrypted tunnel. It’s a great tool that can help you protect your own IP address by anonymizing your web traffic.
Here are some situations when using a VPN for IP protection is highly advisable:
- Accessing blocked websites or services. Some countries may block access to specific websites, social media, and online services. There might also be geo-restrictions due to licensing, copyright, or other issues. So, if you live in or are traveling to countries with internet restrictions, you can use a VPN to safely access blocked sites or services.
- Working remotely. Since employees may need to access their company network and resources outside the office, many businesses implement VPNs for security reasons. If you run a business, consider making it mandatory to use the company’s VPN for employees working remotely. For example, here at Hostinger, we use NordVPN Teams.
- Using public Wi-Fi. As public Wi-Fi is free and readily available, the network can be vulnerable to hackers. Also, most public networks lack user protection or strong security. By enabling a VPN, you’ll bypass the public Wi-Fi ISP network, securing all online communication from threat actors and disguising your identity.
Additionally, virtual private networks come in handy every time you surf the internet but don’t want to leave digital footprints. This also applies when enabling a VPN on your mobile devices.
Without a VPN, websites can gather information whenever you visit them, which includes your session, browsing habits, and the links you click on. In addition, your location can be tracked via the IP address even when the GPS or location services are turned off.
Advertising companies can also customize and show ads based on the above information. This is why ads can sometimes feel targeted and give the impression that certain websites are tracking your digital footprint.
However, remember that a virtual private network is not a complete security solution, as an unreputable VPN provider can be subject to breaches that leak IP addresses. So, keep in mind to choose a reliable provider and check its level of encryption.
Utilize a Proxy Server
Proxy servers and IP address masking provide additional privacy and security for internet users. When utilizing a proxy server, user requests are forwarded through it, which acts as an intermediary between the end user and the destination server.
This process masks the client’s IP address, making it appear as if the requests originate from the proxy web server instead. By concealing the client’s IP address, this type of server helps protect the user’s identity and location, enhancing privacy and anonymity.
A proxy server can also help bypass restrictions imposed by network administrators, ISPs, or governments. Therefore, they can be valuable tools for accessing blocked websites or content, providing users with increased freedom and privacy while navigating the internet.
Consider Tor
Short for The Onion Router, Tor encrypts your information and relays it through a network of servers. By bundling your data into layers of encryption, Tor ensures that your online activities, location, and identity remain private, including from your internet service provider.
To start using Tor, you can download and install the Tor internet browser available for Windows, Mac, Linux, and Android mobile devices. By default, the Tor Browser security level is set to Standard, but you can adjust it from the browser’s settings.
The drawback is that while Tor Browser provides privacy and anonymity during your browsing sessions, it doesn’t conceal your identity when interacting with websites that require login credentials.
Learn More About Cyber Security
Website Security Audit: How to Protect Your Site From Security Breaches
Web Application Security: What It Is, How It Works, and the Best Services
Web Hosting Security Best Practices and What to Look for in Secure Website Hosting
Cloud Security: Best Practices and How to Implement Them

Conclusion
Understanding IP addresses, how they work, and how to protect them from common threats will help you use the internet safely.
An IP address is a unique set of numbers that identify a device, such as computers and mobile phones, in a network. It’s a communication system that rules how networked devices exchange data.
The most commonly used version is IPv4, while its successor is IPv6. The newer Internet Protocol version offers more benefits, such as stronger encryption, more efficient routing, and simplified network configuration.
In terms of types, IP addresses can be categorized based on the network location – private and public. They can also be dynamic or static and shared or dedicated.
Since other people can search for your private and public IP addresses, it’s necessary to be aware of cyber threats and take precautions. To strengthen your IP address reputation management, use a VPN to conceal your IP address when browsing the internet.
We hope this article has been helpful. If you still have questions about IP addresses, feel free to comment below.
What Is an IP Address FAQ
Let’s review the answers to five of the most frequently asked questions regarding IP addresses.
Are There Any VPN Alternatives for Protecting My IP Address?
Zero Trust Network Access (ZTNA) provides secure access to data and applications within a network, keeping your IP address hidden. Using a proxy server can also help hide your IP address, but it doesn’t provide the encryption that VPNs offer.
How Does the Domain Name System (DNS) Relate to IP Addresses?
The role of a domain name system in IP addressing is that it acts as a directory that helps your device find and communicate with other devices on the internet. It translates human-readable domain names into IP addresses.
What Is IPsec, and How Does It Improve IPV6 Security?
IPsec, short for Internet Protocol Security, enhances IP communication security. It’s particularly relevant for IPv6, as it addresses the security vulnerabilities present in earlier versions. By implementing IPsec, IPv6 networks can achieve stronger security measures, protecting against threats and ensuring data privacy and integrity.
What Are the Consequences of IPV4 Address Exhaustion?
The exhaustion of IPv4 addresses has significant consequences for internet connectivity. As more devices connect to the internet, the availability of unique IPv4 addresses diminishes. This could increase Network Address Translation (NAT) use, allowing multiple devices to share the same IP address.
What Is Subnetting and Subnet Masks?
Subnetting divides an IP network into smaller subnetworks called subnets, distinguishing the network and subnet portions. A subnet mask determines which part of the IP address belongs to the network and which part belongs to the host, defining the boundaries between the network, subnet, and host portions.



Comments
March 07 2023
On my phone, this phone, suddenly the IP address seems to be identified as "international" and it keeps my phone from receiving searchse here in the states. Can the IP get changed?
March 10 2023
Hey there! Yes it's possible to change your IP address. One way is to contact your ISP and ask about it. Other and easier method would be to use a VPN and connect to a server that is located in USA. This way your IP will be changed to USA based one and you will see USA specific search results.